No Patch Available Yet for New Major Vulnerability in Ghostscript Interpreter
Tavis Ormandy, a Google Project Zero security researcher, has revealed details about a new major vulnerability discovered in Ghostscript, an interpreter for Adobe’s PostScript and PDF page description languages. Ghostscript is by far the most widely used solution of its kind. The Ghostscript interpreter is…
Dark Tequila Banking Malware Uncovered After 5 Years of Activity
Security researchers at Kaspersky Labs have uncovered a new, complex malware campaign that has been targeting customers of several Mexican banking institutions since at least 2013. Dubbed Dark Tequila, the campaign delivers an advanced keylogger malware that managed to stay under the radar for five years…
Zero-Day In Microsoft’s VBScript Engine Used By Darkhotel APT
A vulnerability in the VBScript engine has been used by hackers working for North Korea to compromise systems targeted by the Darkhotel operation. VBScript is available in the latest versions of Windows and in Internet Explorer 11. In recent versions of Windows, though, Microsoft disabled execution…
JavaScript Web Apps and Servers Vulnerable to ReDoS Attacks
JavaScript web apps and web servers are susceptible to a specific type of vulnerabilities/attacks known as regular expression (regex) denial of service (ReDoS). These vulnerabilities take place when an attacker sends large and complex pieces of text to the open input of a JavaScript-based web…
New PHP Code Execution Attack Puts WordPress Sites at Risk
Sam Thomas, a security researcher from Secarma, has discovered a new exploitation technique that could make it easier for hackers to trigger critical deserialization vulnerabilities in PHP programming language using previously low-risk considered functions. The new technique leaves hundreds of thousands of web applications open to remote…
Necurs Botnet Pushing New Marap Malware
Security researchers from Proofpoint have discovered a new malware strain that they named Marap and which is currently distributed via massive waves of spam emails carrying malicious attachments (malspam). The malware is neither a banking trojan, a remote access trojan (RAT), or ransomware, but a…
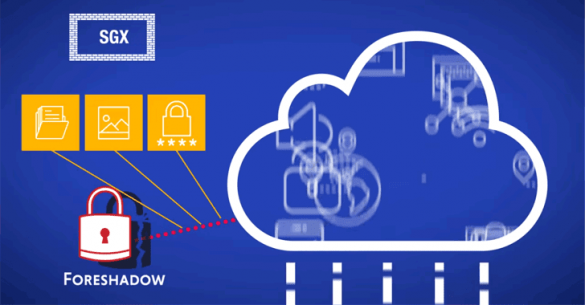
Foreshadow Attacks — 3 New Intel CPU Side-Channel Flaws Discovered
2018 has been quite a tough year for Intel. While the chip-maker giant is still dealing with Meltdown and Spectre processor vulnerabilities, yet another major speculative execution flaw has been revealed in Intel’s Core and Xeon lines of processors that may leave users vulnerable to cyber-attacks. Dubbed Foreshadow, alternatively called…
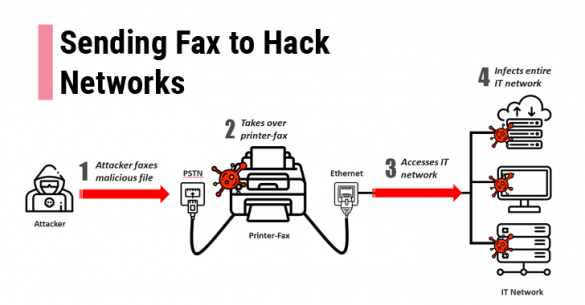
Hackers can compromise your network just by sending a Fax
What maximum a remote attacker can do just by having your Fax machine number? Believe it or not, but your fax number is literally enough for a hacker to gain complete control over the printer and possibly infiltrate the rest of the network connected to…
Oracle warns of CVE-2018-3110 Critical Vulnerability in Oracle Database product, patch it now!
Last week Oracle disclosed a critical vulnerability in its Oracle Database product, the issue tracked as CVE-2018-3110 has received a CVSS score of 9.9, On Friday, Oracle released security patches to address a critical vulnerability affecting its Database product, the company is urging install them as soon…
Hackers Exploiting DLink Routers to Redirect Users to Fake Brazilian Banks
Attackers are targeting DLink DSL modem routers in Brazil and exploiting them to change the DNS settings to a DNS server under the attacker’s control. This then allows them to redirect users attempting to connect to their online banks to fake banking websites that steal the…








Stay connected