BLUE TEAM VS RED TEAM: HOW TO RUN YOUR ENCRYPTED ELF BINARY IN MEMORY AND GO UNDETECTED
Imagine finding yourself in a “hostile” environment, one where you can’t run exploits, tools and applications without worrying about prying eyes spying on you, be they a legitimate system administrator, a colleague sharing an access with you or a software solution that scans the machine…
Unexplored Warfare of 21 Century
1. Introduction In the 21st century, it is almost impossible to even imagine life without technology. Everything from mobile phones to cars everything has embedded systems and computers installed in it which allows the devices to function smartly and fast. These computers are often misunderstood…
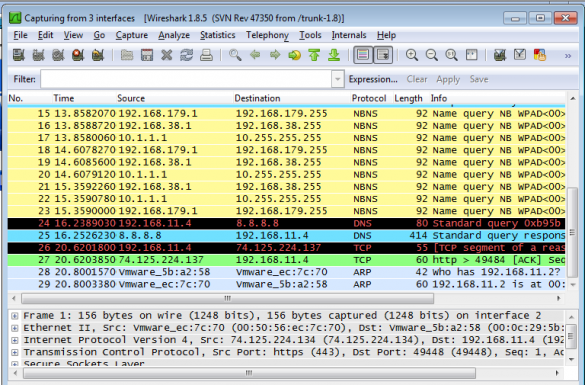
Packet Sniffer to Sniff Sensitive Credentials Only
Author: Roshan Poudel 1.1 Problem Domain According to Nepal telecommunication authority, Nepal’s internet penetration rate is 63% as of 2018. With these increasing number, the responsibility of network monitoring has increased for network and security professionals. They are highly dependent upon the traditional packet sniffer…
Bypassing a null byte POP/POP/RET sequence
1. Preface Structured Exception handlers are commonly exploited when building what’s known as a SEH based buffer overflow, this paper deals with a technique which encompasses DLL injection as a means to bypass a commonly found restriction within the exploitability of an SEH overflow. The…
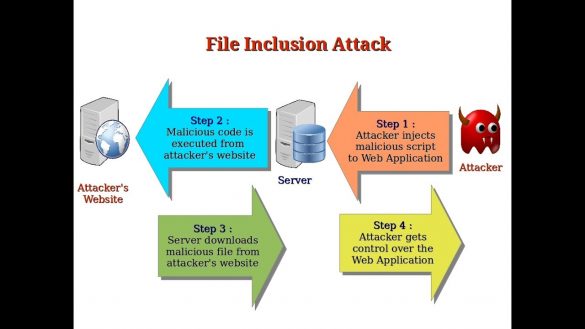
Remote File Inclusion / Local File Inclusion
As with many exploits, remote and local file inclusions are only a problem at the end of theencoding. Of course it takes a second person to have it. Now this article will hopefully give youan idea of protecting your website and most importantly your code…
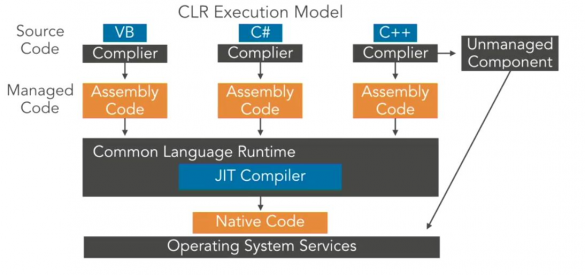
Injecting .NET Ransomware into Unmanaged Process
.Net is a modern, flexible, powerful and memory safe programming language with dozens of libraries and components, and exactly for this reason is the perfect choice to write any sort of malware threats, including ransomwares. The .Net Framework consists of two major components: The Common…
Technical Analysis Of BlueKeep
Introduction: The following text outlines a potential path for exploitation of CVE-2019-0708 (BlueKeep). It is certain that some people will disagree with releasing this text. Reasons why I am releasing: ■ It is released in the spirit of open knowledge. ■ It is an attempt…
A Debugging Primer With CVE-2019-0708
The purpose of this post is to share how one would use a debugger to identify the relevant code path that can trigger the crash. I hope this post will be educational to people that are excited to learning how to use debugger for vulnerability…
Reading Bits in Memory Without Accessing Them
RAMBleed is a side-channel attack that enables an attacker to read out physical memory belonging to other processes. The implications of violating arbitrary privilege boundaries are numerous, and vary in severity based on the other software running on the target machine. As an example, in…
Analysis of CVE-2019-0708 (BlueKeep)
Binary Diffing As always, I started with a BinDiff of the binaries modified by the patch (in this case there is only one: TermDD.sys). Below we can see the results. A BinDiff of TermDD.sys pre and post patch. Most of the changes turned out to…








Stay connected