ARM EXPLOITATION FOR IoT
Authored by Andrea Sindoni Introduction and motivation A year ago while I was attending a conference, I’ve noticed that price tag for the proposed ARM exploitation cource for IoT was quite substantial and decided to write my own to allow those who can’t afford to spend…
Performing Passive Analysis of Process Control Networks (PCNs)
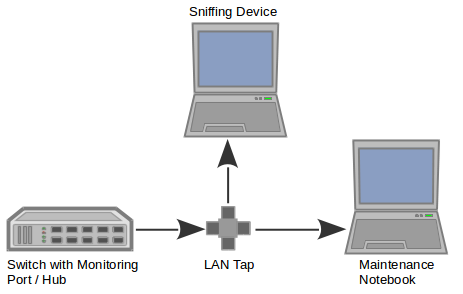
In recent years there has been an increased push to secure critical ICS infrastructures by introducing information security management systems. One of the first steps in the ISMS lifecycle is to identify which assets are present in the infrastructure and to determine which ones are…
US CERT update on Home Network Security
What is home network security? Home network security refers to the protection of a network that connects devices to each other and to the internet within a home. Whether it’s staying in touch with friends and family, paying your bills electronically, or teleworking, the internet…


Stay connected