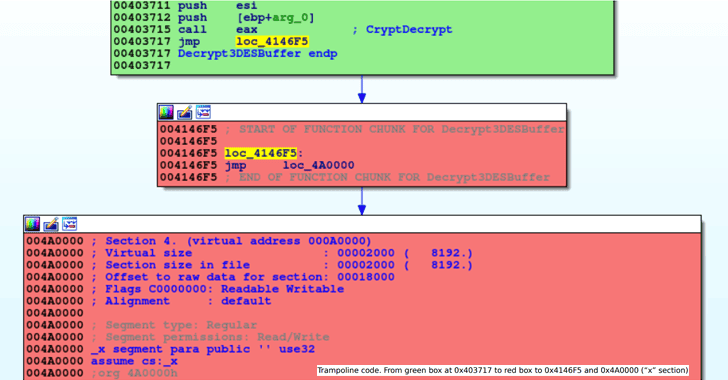
Most LokiBot samples in the wild are “hijacked” versions of the original malware
Hacker himself got hacked. It turns out that most samples of the LokiBot malware being distributed in the wild are modified versions of the original sample, a security researcher has learned. Targeting users since 2015, LokiBot is a password and cryptocoin-wallet stealer that can harvest…
ARM EXPLOITATION FOR IoT
Authored by Andrea Sindoni Introduction and motivation A year ago while I was attending a conference, I’ve noticed that price tag for the proposed ARM exploitation cource for IoT was quite substantial and decided to write my own to allow those who can’t afford to spend…
Using a simple Google query to mine passwords from dozens of public Trello boards
Kushagra Pathak, a Security researcher, published a great text related to mining confidential data using Google search. We have reprinted his text below, while you can find original text at following URL: https://medium.freecodecamp.org/discovering-the-hidden-mine-of-credentials-and-sensitive-information-8e5ccfef2724 How I used a simple Google query to mine passwords from dozens…
Password-Guessing Was Used to Hack Gentoo Linux Github Account
Maintainers of the Gentoo Linux distribution have now revealed the impact and “root cause” of the attack that saw unknown hackers taking control of its GitHub account last week and modifying the content of its repositories and pages. The hackers not only managed to change the content…
wolfMQTT Client Library Adds End-to-End Encryption for M2M and IoT
WolfSSL recently released the wolfMQTT client library, a security add-on that provides SSL/TLS encryption for the Message Queuing Telemetry Transport (MQTT) protocol. MQTT is a publisher/subscriber based architecture, in which systems communicate among each other by publishing messages and subscribing to topics through TCP/IP network…
Pentester’s Guide to IoT Penetration Testing
IoT penetration testing specifics from a certified ethical hacker with 5+ years of experience. With the growing risk to IoT security, penetration testing vendors face multiple queries from companies and individuals, who want their IoT environment to be tested against potential cyber-attacks. Usually, security service providers…
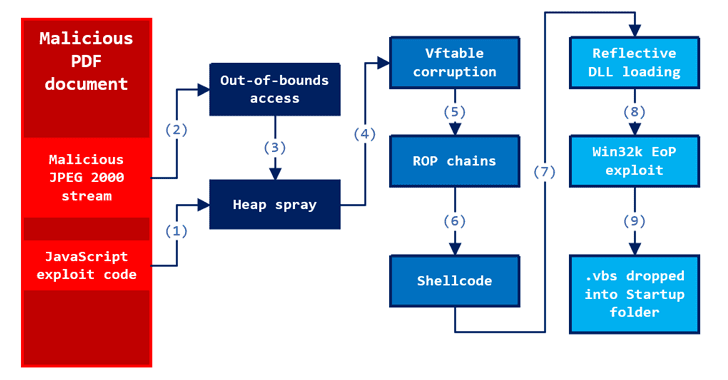
Two Zero-Day Exploits Found After Someone Uploaded ‘Unarmed’ PoC to VirusTotal
Security researchers at Microsoft have unveiled details of two critical and important zero-day vulnerabilities that had recently been discovered after someone uploaded a malicious PDF file to VirusTotal, and get patched before being used in the wild. In late March, researchers at ESET found a…
Cryptojacking Rises as Ransomware Declines, Cyber Security Researchers Find
Two of the leading international cyber security firms, one from Russia and one from the USA, have both published their finds at the end of June showing an increase in the malware threats market share of cryptojacking at the expense of ransomware New Crypto Crime…
Typeform, Popular Online Survey Software, Suffers Data Breach
Typeform, the popular Spanish-based online data collection company specializes in form building and online surveys for businesses worldwide, has today disclosed that the company has suffered a data breach that exposed partial data of its some users. The company identified the breach on June 27th,…
RAMpage Attack Explained—Exploiting RowHammer On Android Again!
A team of security researchers has discovered a new set of techniques that could allow hackers to bypass all kind of present mitigations put in place to prevent DMA-based Rowhammer attacks against Android devices. Dubbed RAMpage, the new technique (CVE-2018-9442) could re-enable an unprivileged Android…







Stay connected