New WiFi Authentication Vulnerabilities Discovered
One vulnerability affects Android, ChromeOS and Linux devices connecting to enterprise WiFi networks, another affects home WiFi using a Linux device as a wireless access point. Two new vulnerabilities in open-source WiFi software allow attackers to trick victims into connecting to malicious clones of trusted…
Siemens Parasolid
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to leverage the vulnerability to perform remote code execution in the context of the current process. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products of Siemens are affected: 3.2…
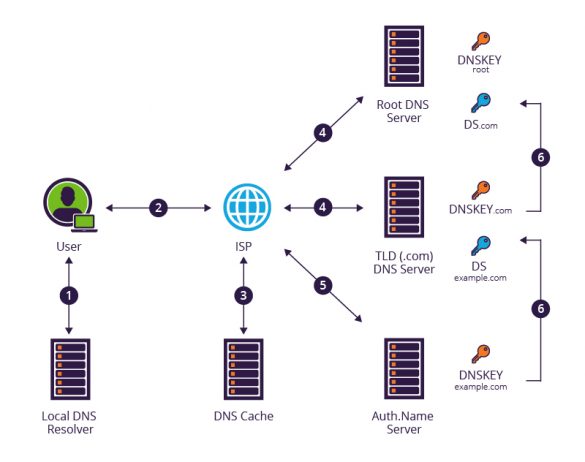
CVE-2023-50387: KeyTrap – Extreme CPU consumption in DNSSEC validator
CVE: CVE-2023-50387 Title: KeyTrap – Extreme CPU consumption in DNSSEC validator Document version: 2.0 Posting date: 13 February 2024 Program impacted: BIND 9 Versions affected: BIND (Versions prior to 9.11.37 were not assessed.) BIND Supported Preview Edition (Versions prior to 9.11.37-S1 were not assessed.) Severity: High Exploitable: Remotely Description: The processing of…
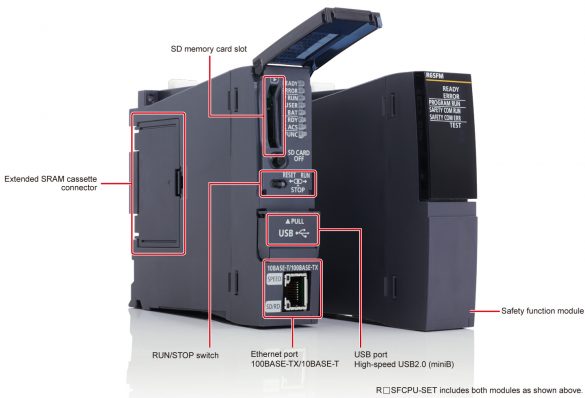
Mitsubishi Electric MELSEC iQ-R Series Safety CPU
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a non-administrator user to disclose the credentials (user ID and password) of a user with a lower access level than themselves. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS Mitsubishi Electric reports that the…
Cisco Expressway Series Cross-Site Request Forgery Vulnerabilities
Summary Affected Products Details The vulnerabilities are not dependent on one another. Exploitation of one of the vulnerabilities is not required to exploit another vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other…
glibc qsort() Out-Of-Bounds Read / Write
Summary We discovered a memory corruption in the glibc’s qsort() function, due to a missing bounds check. To be vulnerable, a program must call qsort() with a nontransitive comparison function (a function cmp(int a, int b) that returns (a – b), for example) and with…
Heap-based buffer overflow in the glibc’s syslog ()
Summary -Heap-based buffer overflow in the glibc’s syslog () We discovered a heap-based buffer overflow in the GNU C Library’s __vsyslog_internal() function, which is called by both syslog() and vsyslog(). This vulnerability was introduced in glibc 2.37 (in August 2022) by the following commit: https://sourceware.org/git?p=glibc.git;a=commit;h=52a5be0df411ef3ff45c10c7c308cb92993d15b1…
Cisco Unified Communications Products Remote Code Execution Vulnerability
Summary Affected Products Products Confirmed Not Vulnerable Only products listed in the Vulnerable Products section of this advisory are known to be affected by this vulnerability. Cisco has confirmed that this vulnerability does not affect the following Cisco products: Workarounds Additionally, follow the best practices that are…
Passive SSH Key Compromise via Lattices
ABSTRACTWe demonstrate that a passive network attacker can opportunistically obtain private RSA host keys from an SSH server that experiences a naturally arising fault during signature computation. In prior work, this was not believed to be possible for the SSH protocol because the signature included…
VMware Releases Security Advisory for Aria Operations
Security Advisory: VMSA-2024-0001 1. Impacted Products 2. Introduction A Missing Access Control vulnerability in Aria Automation has been privately reported to VMware. Updates are available to remediate this vulnerability in affected VMware products. 3. Aria Automation Missing Access Control Vulnerability (CVE-2023-34063) Description: Aria Automation contains…









Stay connected