Siemens OpenSSL Vulnerability in Industrial Products (Update E)
1. EXECUTIVE SUMMARY CVSS v3 5.9 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: Industrial Products Vulnerability: Cleartext Transmission of Sensitive Information 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-18-226-02 Siemens OpenSSL Vulnerability in Industrial Products (Update D) that was…
Siemens SCALANCE, SIMATIC, RUGGEDCOM, and SINAMICS Products (Update F)
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits are available. Vendor: Siemens Equipment: SCALANCE, SIMATIC, RUGGEDCOM, and SINAMICS Products Vulnerabilities: Security Features 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-17-318-01 Siemens SCALANCE,…
Omron CX-Programmer
1. EXECUTIVE SUMMARY CVSS v3 6.6 ATTENTION: Low skill level to exploit Vendor: Omron Equipment: CX-Programmer within CX-One Vulnerability: Use After Free 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute code under the privileges of the application. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…
Rockwell Automation Stratix 5400/5410/5700 and ArmorStratix 5700
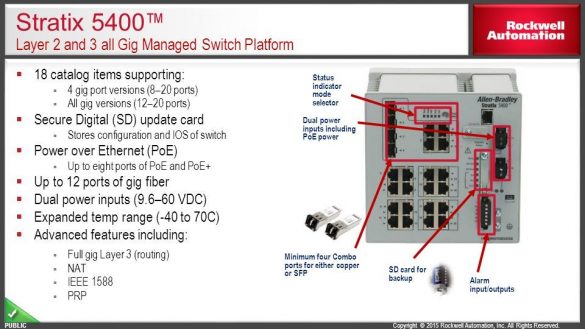
1. EXECUTIVE SUMMARY ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: Stratix 5400/5410/5700, ArmorStratix 5700 Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated remote attacker to cause a memory leak on an affected device, which may cause the…
Rockwell Automation Stratix 5400/5410/5700/8000/8300 and ArmorStratix 5700
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: Stratix 5400/5410/5700/8000/8300, ArmorStratix 5700 Vulnerabilities: Resource Management Errors, Improper Input Validation 2. RISK EVALUATION Successful exploitation of these vulnerabilities could result in a denial-of-service condition or time synchronization issues across the network…
Rockwell Automation Stratix 5950
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: Stratix 5950 Vulnerability: Improper Input Validation 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to cause an affected device to reload. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…
CVE-2019-0211 Apache flaw allows getting root access via script
The privilege escalation vulnerability (CVE-2019-0211) affecting the Apache HTTP server could be exploited by users with the right to write and run scripts to gain root on Unix systems An important privilege escalation vulnerability (CVE-2019-0211) affecting the Apache HTTP server could be exploited by users…
Advantech WebAccess/SCADA
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess/SCADA Vulnerabilities: Command Injection, Stack-based Buffer Overflow, Improper Access Control 2. RISK EVALUATION Successful exploitation of these vulnerabilities may cause a denial of service and allow remote code execution. 3. TECHNICAL DETAILS 3.1…
WinRAR CVE-2018-20250 flaw exploited in multiple campaigns
The recently patched vulnerability affecting the popular archiver utility WinRAR has been exploited to deliver new malware to targeted users. A recently patched vulnerability affecting the popular archiver utility WinRAR it becoming a commodity in the cybercrime underground, experts reported it has been exploited to deliver new…
Rockwell Automation PowerFlex 525 AC Drives
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: PowerFlex 525 AC Drives Vulnerability: Resource Exhaustion 2. RISK EVALUATION Successful exploitation of this vulnerability could result in resource exhaustion, denial of service, and/or memory corruption. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS…










Stay connected