1. EXECUTIVE SUMMARY
- CVSS v3 9.8
- ATTENTION: Exploitable remotely/low skill level to exploit
- Vendor: Triangle MicroWorks
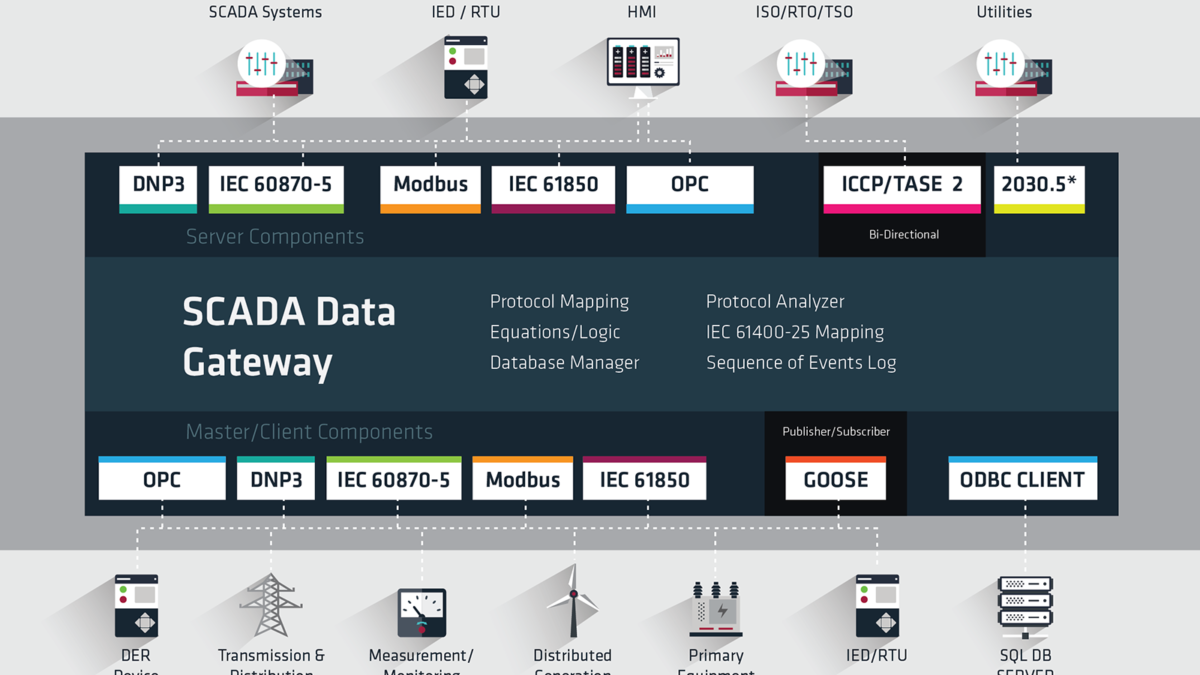
- Equipment: SCADA Data Gateway
- Vulnerabilities: Stacked-based Buffer Overflow, Out-of-Bounds Read, Type Confusion
2. RISK EVALUATION
These vulnerabilities allow remote attackers to execute arbitrary code and disclose on affected installations of Triangle Microworks SCADA Data Gateway with DNP3 Outstation channels. Authentication is not required to exploit these vulnerabilities.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following versions of SCADA Data Gateway software are affected:
- 2.41.0213 through 4.0.122
3.2 VULNERABILITY OVERVIEW
3.2.1 STACK-BASED BUFFER OVERFLOW CWE-121
This vulnerability allows remote attackers cause a denial-of-service condition due to a lack of proper validation of the length of user-supplied data, prior to copying it to a fixed-length stack-based buffer. Authentication is not required to exploit this vulnerability.
CVE-2020-10615 has been assigned to this vulnerability. A CVSS v3 base score of 7.5 has been assigned; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.2.2 OUT-OF-BOUNDS READ CWE-125
This vulnerability allows remote attackers to disclose sensitive information due to the lack of proper validation of user-supplied data, which can result in a read past the end of an allocated structure. Authentication is not required to exploit this vulnerability. Only applicable to installations using DNP3 Data Sets.
CVE-2020-10613 has been assigned to this vulnerability. A CVSS v3 base score of 5.3 has been assigned; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N).
3.2.3 ACCESS OF RESOURCE USING INCOMPATIBLE TYPE (‘TYPE CONFUSION’) CWE-843
This vulnerability allows remote attackers to execute arbitrary code due to the lack of proper validation of user-supplied data, which can result in a type confusion condition. Authentication is not required to exploit this vulnerability. Only applicable to installations using DNP3 Data Sets.
CVE-2020-10611 has been assigned to this vulnerability. A CVSS v3 base score of 9.8 has been assigned; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Energy, Water and Wastewater Systems
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: United States
3.4 RESEARCHER
Incite Team of Steven Seeley and Chris Anastasio, and Tobias Scharnowski, Niklas Breitfeld, and Ali Abbasi working with Trend Micro’s Zero Day Initiative reported these vulnerabilities to CISA.
4. MITIGATIONS
Triangle Microworks recommends users update to Version 4.0.123
Please contact Triangle MicroWorks support for additional details.
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability. Specifically, users should:
- Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
- Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
- When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on us-cert.gov. Several recommended practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage on us-cert.gov in the Technical Information Paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing any suspected malicious activity should follow their established internal procedures and report their findings to CISA for tracking and correlation against other incidents.
No known public exploits specifically target these vulnerabilities.
Source:

Stay connected