Siemens KTK, SIDOOR, SIMATIC, and SINAMICS
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: KTK, SIDOOR, SIMATIC, and SINAMICS Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability could create a denial-of-service condition. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following Siemens products are…
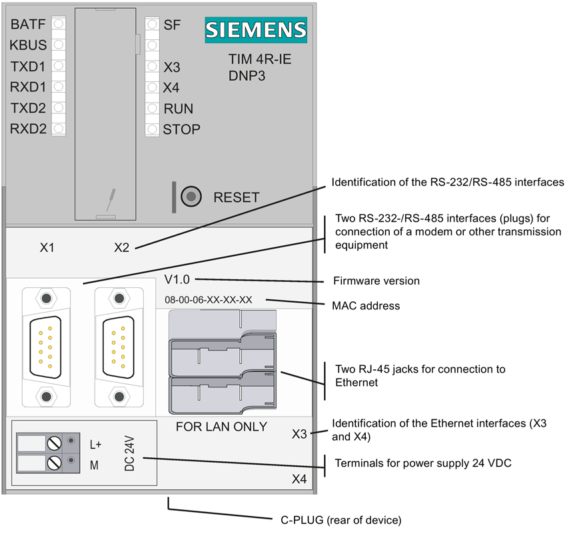
Siemens TIM 3V-IE and 4R-IE Family Devices
1. EXECUTIVE SUMMARY CVSS v3 9.0 ATTENTION: Exploitable remotely Vendor: Siemens Equipment: TIM 3V-IE and 4R-IE Family Devices Vulnerability: Active Debug Code 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated attacker with network access to gain full control over the device. 3. TECHNICAL DETAILS 3.1 AFFECTED…
Siemens SIMATIC S7 (Update B)
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: SIMATIC S7 Vulnerability: Uncontrolled Resource Consumption (Resource Exhaustion) 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-20-042-05 Siemens SIMATIC S7 (Update A) that was published March 10,…
Siemens TIA Portal (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Siemens Equipment: TIA Portal Vulnerability: Path Traversal 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-20-014-05 Siemens TIA Portal that was published January 14, 2020, to the ICS webpage on…
Siemens PROFINET Devices (Update E)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: PROFINET Devices Vulnerability: Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the advisory update titled ICSA-19-283-02 Siemens PROFINET Devices (Update D) that was published March 10, 2020, to…
Siemens Industrial Products (Update F)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Siemens Equipment: Industrial Products Vulnerabilities: Integer Overflow or Wraparound, Uncontrolled Resource Consumption 2. UPDATE INFORMATION This updated advisory is a follow-up to the updated advisory titled ICSA-19-253-03 Siemens Industrial Products (Update E) that was published…
Rockwell Automation RSLinx Classic
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Low skill level to exploit Vendor: Rockwell Automation Equipment: RSLinx Classic Vulnerability: Incorrect Permission Assignment for Critical Resource 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a local authenticated attacker to execute malicious code when opening RSLinx Classic. 3. TECHNICAL…
BD Pyxis MedStation and Pyxis Anesthesia (PAS) ES System
1. EXECUTIVE SUMMARY CVSS v3 6.8 ATTENTION: Low skill level to exploit Vendor: Becton, Dickinson and Company (BD) Equipment: Pyxis MedStation and Pyxis Anesthesia (PAS) ES System Vulnerability: Protection Mechanism Failure 2. RISK EVALUATION The affected BD medical devices utilize a method of software application implementation called “kiosk mode.”…
Advantech WebAccess/NMS
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Advantech Equipment: WebAccess/NMS Vulnerabilities: Unrestricted Upload of File with Dangerous Type, SQL Injection, Relative Path Traversal, Missing Authentication for Critical Function, Improper Restriction of XML External Entity Reference, OS Command Injection 2. RISK EVALUATION Successful…
GE Digital CIMPLICITY
1. EXECUTIVE SUMMARY CVSS v3 6.0 ATTENTION: Low skill level to exploit Vendor: GE Digital Equipment: CIMPLICITY Vulnerability: Improper Privilege Management 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an adversary to modify the systemwide CIMPLICITY configuration, leading to the arbitrary execution of code. 3. TECHNICAL DETAILS…










Stay connected