Philips Tasy EMR
1. EXECUTIVE SUMMARY CVSS v3 4.1 ATTENTION: Low skill level to exploit Vendor: Philips Equipment: Tasy EMR Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could impact or compromise patient confidentiality and system integrity. Philips’ analysis has shown these issues, if fully exploited, may allow attackers…
Rockwell Automation CompactLogix 5370
1. EXECUTIVE SUMMARY CVSS v3 8.6 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: CompactLogix 5370 Vulnerabilities: Uncontrolled Resource Consumption, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a remote attacker to render the web server unavailable and/or place the controller…
Docker Hub Database hacked, 190,000 users impacted
Docker became aware of unauthorized access to a Docker Hub database that exposed sensitive information for roughly 190,000 users. Docker notified its users that an unauthorized entity gained access to a Docker Hub database that exposed sensitive information for roughly 190,000 users. The exposed information…
Orpak SiteOmat
EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits available Vendor: Orpak (acquired by Gilbarco Veeder-Root) Equipment: SiteOmat Vulnerabilities: Use of Hard-coded Credentials, Cross-site Scripting, SQL Injection, Missing Encryption of Sensitive Data, Code Injection, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities…
New Exploits for Unsecure SAP Systems
Summary The Cybersecurity and Infrastructure Security Agency (CISA) is issuing this activity alert in response to recently disclosed exploits that target unsecure configurations of SAP components. Technical Details A presentation at the April 2019 Operation for Community Development and Empowerment (OPCDE) cybersecurity conference describes SAP…
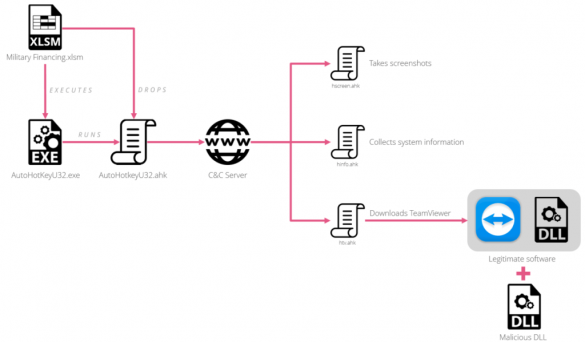
Targeted Attacks hit multiple embassies with Trojanized TeamViewer
CheckPoint firm uncovered a cyber espionage campaign leveraging a weaponized version of TeamViewer to target officials in several embassies in Europe. Security experts at CheckPoint uncovered a cyber espionage campaign leveraging a weaponizedversion of TeamViewer and malware disguised as a top-secret US government document to target officials in…
Fujifilm FCR Capsula X/Carbon X
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Fujifilm Equipment: FCR Capsula X/Carbon X Vulnerabilities: Uncontrolled Resource Consumption, Improper Access Control 2. RISK EVALUATION Successful exploitation of these vulnerabilities could result in a denial-of-service condition in affected cassette reader units, causing potential image…
Rockwell Automation MicroLogix 1400 and CompactLogix 5370 Controllers
1. EXECUTIVE SUMMARY CVSS v3 7.1 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Rockwell Automation Equipment: MicroLogix 1400 and CompactLogix 5370 Controllers Vulnerability: Open Redirect 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote unauthenticated attacker to input a malicious link redirecting users to a…
New zero-day vulnerability CVE-2019-0859 in win32k.sys
In March 2019, our automatic Exploit Prevention (EP) systems detected an attempt to exploit a vulnerability in the Microsoft Windows operating system. Further analysis of this event led to us discovering a zero-day vulnerability in win32k.sys. It was the fifth consecutive exploited Local Privilege Escalation…
New DNS Hijacking Attacks
DNS hijacking isn’t new, but this seems to be an attack of uprecidented scale: Researchers at Cisco’s Talos security division on Wednesday revealed that a hacker group it’s calling Sea Turtle carried out a broad campaign of espionage via DNS hijacking, hitting 40 different organizations. In the…










Stay connected