Mitsubishi Electric GOT and Tension Controller (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: GOT and Tension Controller Vulnerabilities: Improper Handling of Exceptional Conditions, Improper Input Validation ——— Begin Update A Part 1 of 2 ——— Mitsubishi Electric PSIRT has informed CISA that further research has shown the…
ICS Advisory (ICSA-22-090-01)
1. EXECUTIVE SUMMARY CVSS v3 5.5 ATTENTION: Low attack complexity Vendor: Schneider Electric Equipment: SCADAPack Workbench Vulnerability: Improper Restriction of XML External Entity Reference 2. RISK EVALUATION Successful exploitation of this vulnerability could result from exfiltration of data from local files to a remote system controlled by an attacker….
Siemens RUGGEDCOM Devices Vulnerability
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: RUGGEDCOM Devices Vulnerability: Missing Encryption of Sensitive Data 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an authorized threat actor to obtain privileges to access passwords. 3. TECHNICAL DETAILS…
Four Cyber Security Risks and How to Address Them
Security should be at the top of the mind for any organization. It has been estimated that damages from cyber crime would cost around $6 trillion annually by 2021. With growing threats to information systems and data, it is extremely important for organizations to remain…
Default Passwords Aid Satori IoT Botnet Attacks
Researchers at Netlab 360 detected a surge in malicious activity scanning and infecting several IoT devices, attempting to make them part of Satori, a variant of the Mirai IoT botnet that is used to take down websites and mine digital coins. Experts point to lack of oversight…
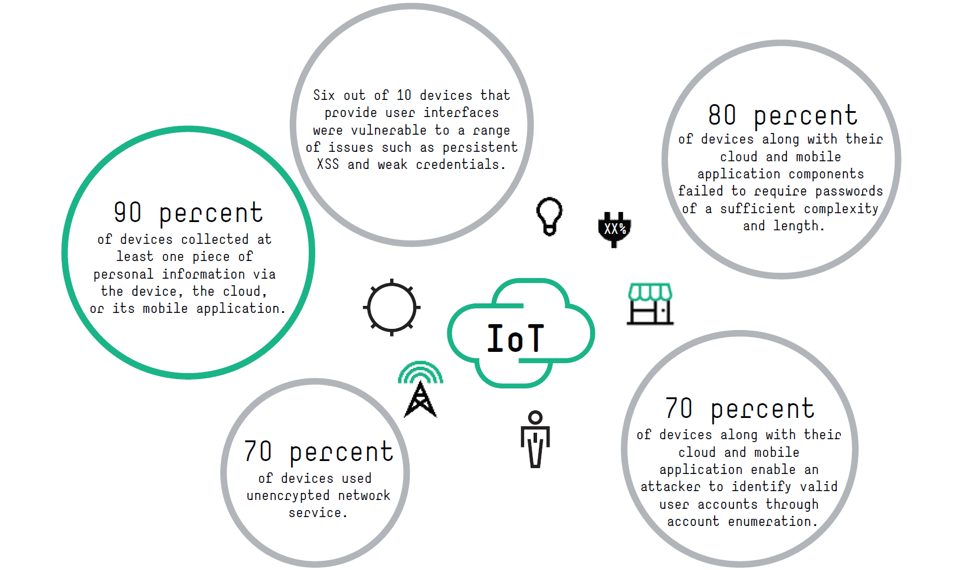
Google Home’s data leak proves the IoT is still deeply flawed
Google / WIRED / Artizarus The Internet of Things (IoT) security problem isn’t going away. The connected network of billions of devices – from smart doorbells to office printers – is regularly found to have privacy problems and be open to attack by potential hackers….
Magento Hackers Using Simple Evasion Trick to Reinfect Sites With Malware
Security researchers have been warning of a new trick that cybercriminals are leveraging to hide their malicious code designed to re-introduce the infection to steal confidential information from Magento based online e-commerce websites. So, if you have already cleaned up your hacked Magento website, there…
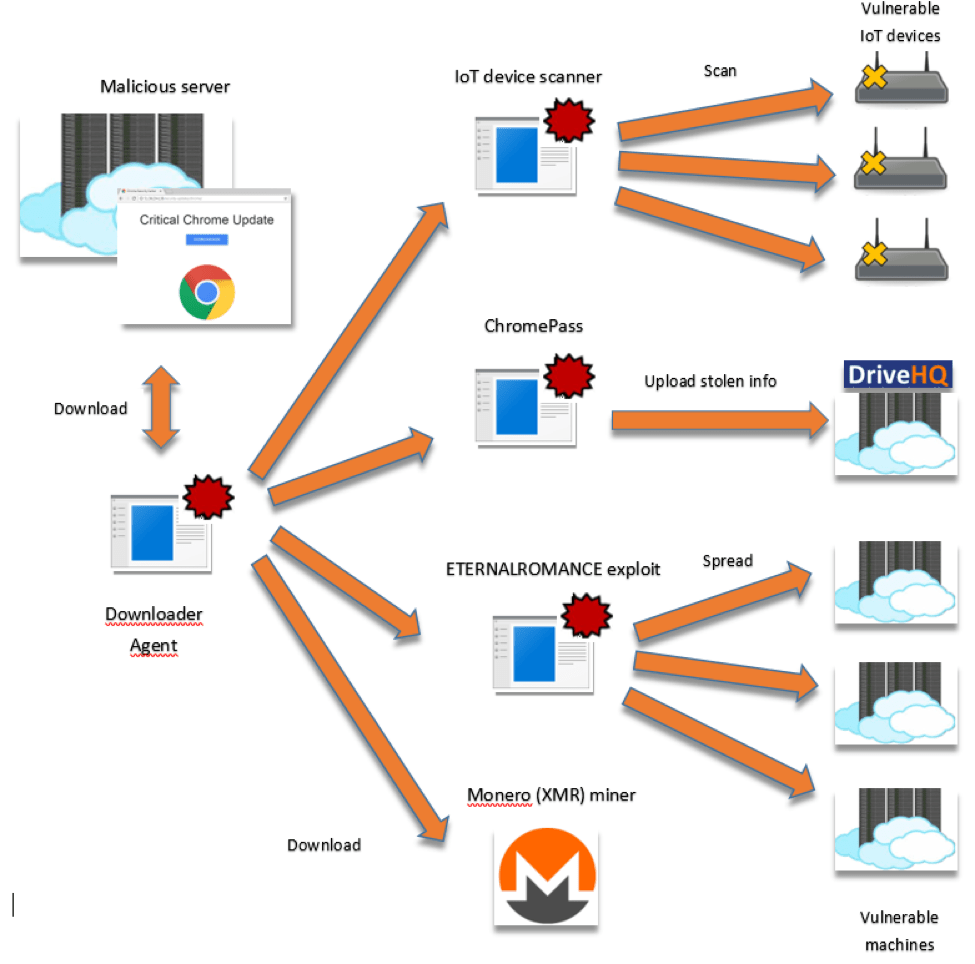
GDPR – PyRoMineIoT spreads via EternalRomance exploit and targets targets IoT devices in Iran and Saudi Arabia.
Fortinet discovered PyRoMineIoT, a new strain of crypto-currency miner that exploits the NSA-linked EternalRomance exploit to spread. PyRoMineIoT is a new strain of crypto-currency miner that exploits the NSA-linked EternalRomance remote code execution exploit to spread, the malware also abuses infected machines to scan for vulnerable Internet of Things (IoT) devices….
Microsoft Calls On Linux for Its New IoT Security Platform
Microsoft has opted to use its own version of a Linux operating system instead of Windows 10 to drive its new Azure Sphere solution for securely connecting Internet of Things devices. Microsoft introduced Azure Sphere last week at the RSA security conference in San Francisco….
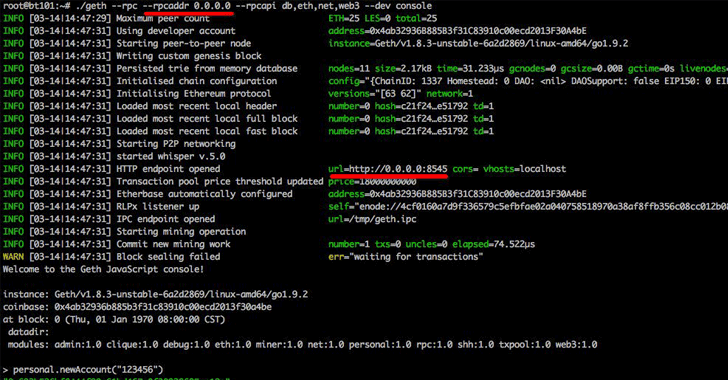
Hackers Stole Over $20 Million in Ethereum from Insecurely Configured Clients
Researchers have been warning about cyber attacks wherein attackers made over 20 million dollars by hijacking insecurely configured Ethereum nodes exposed on the Internet. Qihoo 360 Netlab in March tweeted about a group of cybercriminals who were scanning the Internet for port 8545 to find insecure geth…








Stay connected