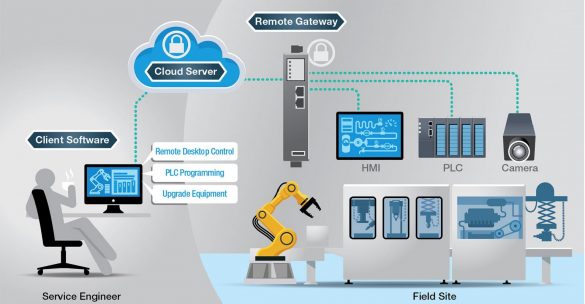
Five Issues Facing Secure Remote Access to IIoT Machines
The Industrial Internet of Things (IIoT) is changing the way business owners view their factories by giving them real-time data from machines and devices in the field that let them monitor and control production. Overall equipment effectiveness (OEE) and zero equipment downtime are no longer…
Progress Launches AWS-Backed IIoT Anomaly Detection Service
Progress announced on Thursday the launch of a new self-service anomaly detection and prediction option for the IIoT market that leverages AWS. Application development and deployment company Progress announced on Thursday the launch of a new self-service anomaly detection and prediction option for the Industrial…
Particle Mesh – A Mesh-Enabled IoT Development Kits.
Particle, which has been known for its collection of IoT focused development boards, and its Internet of Things (IoT) platform (Particle Cloud) has launched a new set of mesh network-enabled IoT development kits called Particle Mesh. Particle Mesh is expected to provide developers more insight…
Intelligent IoT Vulnerability Scanner for communication service providers launched to assess and predict cybersecurity risks
Dojo by BullGuard, a provider of IoT security platform for Communication Service Providers (CSPs), has launched the Dojo Intelligent IoT Vulnerability Scanner for CSPs. Designed as an easy-to-use, free app for customers, the Dojo Intelligent Scanner is powered by the Dojo IoT Security Intelligent Platform (DIP), a…
How Mirai spawned the current IoT malware landscape
When, in late 2016, US-based DNS provider Dyn suffered a massive DDoS attack that it resulted in the temporary unavailability of many popular online services, the name of the Mirai malware became instantly known outside the cybersecurity industry. Since then, we’ve come to know the…
Operation Prowli Profits On Weak IoT Devices, Servers
A malicious campaign has compromised more than 40,000 machines globally, carrying out traffic-hijacking and cryptomining. Researchers at Guardicore Labs, who called the campaign Operation Prowli, said it targets a variety of platforms – including Drupal CMS websites, WordPress sites, backup servers running HP Data Protector,…
Z-Wave Downgrade Attack Left Over 100 Million IoT Devices Open to Hackers
Researchers have found that even after having an advanced encryption scheme in place, more than 100 million Internet-of-Things (IoT) devices from thousands of vendors are vulnerable to a downgrade attack that could allow attackers to gain unauthorized access to your devices. The issue resides in…
US CERT update on Home Network Security
What is home network security? Home network security refers to the protection of a network that connects devices to each other and to the internet within a home. Whether it’s staying in touch with friends and family, paying your bills electronically, or teleworking, the internet…








Stay connected