Hitachi Energy MicroSCADA Pro/X SYS600
1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Hitachi Energy Equipment: MicroSCADA Pro/X SYS600 Vulnerabilities: Observable Discrepancy, HTTP Request Smuggling, Classic Buffer Overflow, Improper Certificate Validation, Improper Restriction of Operations within the Bounds of a Memory Buffer, Exposure of Sensitive Information to an Unauthorized Actor…
Mitsubishi Electric MELSEC-Q Series C Controller Module
1. EXECUTIVE SUMMARY CVSS v3 9.0 ATTENTION: Exploitable remotely Vendor: Mitsubishi Electric Equipment: MELSEC-Q Series C Controller Module Vulnerability: Heap-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of this vulnerability could cause a denial-of-service condition or allow remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions…
Mitsubishi Electric GOT and Tension Controller (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: GOT and Tension Controller Vulnerabilities: Improper Handling of Exceptional Conditions, Improper Input Validation ——— Begin Update A Part 1 of 2 ——— Mitsubishi Electric PSIRT has informed CISA that further research has shown the…
ICS Advisory (ICSA-22-090-01)
1. EXECUTIVE SUMMARY CVSS v3 5.5 ATTENTION: Low attack complexity Vendor: Schneider Electric Equipment: SCADAPack Workbench Vulnerability: Improper Restriction of XML External Entity Reference 2. RISK EVALUATION Successful exploitation of this vulnerability could result from exfiltration of data from local files to a remote system controlled by an attacker….
Siemens RUGGEDCOM Devices Vulnerability
1. EXECUTIVE SUMMARY CVSS v3 5.3 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: RUGGEDCOM Devices Vulnerability: Missing Encryption of Sensitive Data 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an authorized threat actor to obtain privileges to access passwords. 3. TECHNICAL DETAILS…
Orpak SiteOmat
EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit/public exploits available Vendor: Orpak (acquired by Gilbarco Veeder-Root) Equipment: SiteOmat Vulnerabilities: Use of Hard-coded Credentials, Cross-site Scripting, SQL Injection, Missing Encryption of Sensitive Data, Code Injection, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities…
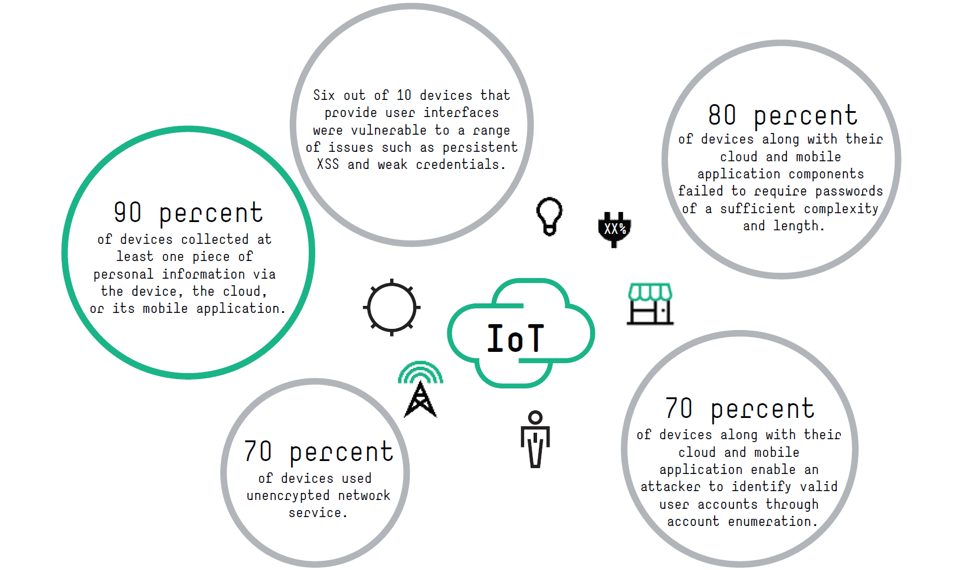
Four Cyber Security Risks and How to Address Them
Security should be at the top of the mind for any organization. It has been estimated that damages from cyber crime would cost around $6 trillion annually by 2021. With growing threats to information systems and data, it is extremely important for organizations to remain…
Amazon Fire TV and Fire TV Stick Miner Infections on the Rise
Following the large number of viruses that are being developed for Android and iOS devices, latest news is that a large number of Amazon Fire TV and Fire TV Stick devices are being targeted by cryptocurrency miners. The hackers have developed numerous forms of malicious…
How Mirai spawned the current IoT malware landscape
When, in late 2016, US-based DNS provider Dyn suffered a massive DDoS attack that it resulted in the temporary unavailability of many popular online services, the name of the Mirai malware became instantly known outside the cybersecurity industry. Since then, we’ve come to know the…
Operation Prowli Profits On Weak IoT Devices, Servers
A malicious campaign has compromised more than 40,000 machines globally, carrying out traffic-hijacking and cryptomining. Researchers at Guardicore Labs, who called the campaign Operation Prowli, said it targets a variety of platforms – including Drupal CMS websites, WordPress sites, backup servers running HP Data Protector,…










Stay connected