Magento Hackers Using Simple Evasion Trick to Reinfect Sites With Malware
Security researchers have been warning of a new trick that cybercriminals are leveraging to hide their malicious code designed to re-introduce the infection to steal confidential information from Magento based online e-commerce websites. So, if you have already cleaned up your hacked Magento website, there…
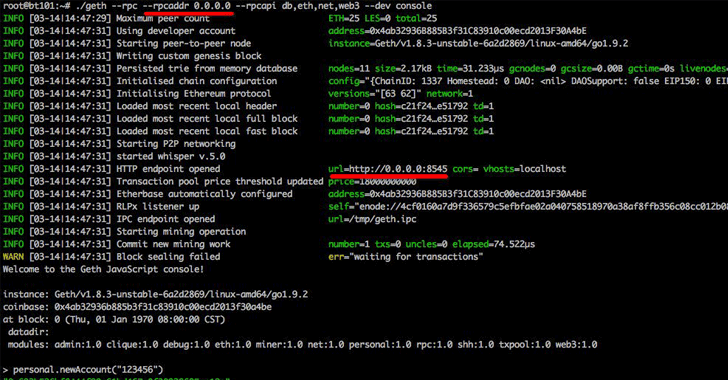
Hackers Stole Over $20 Million in Ethereum from Insecurely Configured Clients
Researchers have been warning about cyber attacks wherein attackers made over 20 million dollars by hijacking insecurely configured Ethereum nodes exposed on the Internet. Qihoo 360 Netlab in March tweeted about a group of cybercriminals who were scanning the Internet for port 8545 to find insecure geth…
Amazon Fire TV and Fire TV Stick Miner Infections on the Rise
Following the large number of viruses that are being developed for Android and iOS devices, latest news is that a large number of Amazon Fire TV and Fire TV Stick devices are being targeted by cryptocurrency miners. The hackers have developed numerous forms of malicious…
How Mirai spawned the current IoT malware landscape
When, in late 2016, US-based DNS provider Dyn suffered a massive DDoS attack that it resulted in the temporary unavailability of many popular online services, the name of the Mirai malware became instantly known outside the cybersecurity industry. Since then, we’ve come to know the…
Operation Prowli Profits On Weak IoT Devices, Servers
A malicious campaign has compromised more than 40,000 machines globally, carrying out traffic-hijacking and cryptomining. Researchers at Guardicore Labs, who called the campaign Operation Prowli, said it targets a variety of platforms – including Drupal CMS websites, WordPress sites, backup servers running HP Data Protector,…
Z-Wave Downgrade Attack Left Over 100 Million IoT Devices Open to Hackers
Researchers have found that even after having an advanced encryption scheme in place, more than 100 million Internet-of-Things (IoT) devices from thousands of vendors are vulnerable to a downgrade attack that could allow attackers to gain unauthorized access to your devices. The issue resides in…
Nintendo Switch has been hacked
HACKERS have managed to hack Nintendo’s latest video game console, thanks to a hard-coded flaw in the Nvidia Tegra X1 silicon inside. Read More
Tesla public cloud environment hacked, attackers accessed ‘non-public’ company data
Building a slide deck, pitch, or presentation? Here are the big takeaways: 73% of organizations allow the root user account to be used to perform activities, which goes against security best practices. — RedLock, 2018 Hackers broke into Tesla’s public cloud environment and gained access…
Artificial intelligence could supercharge hacking and election meddling, study warns
Breaking News Emails Get breaking news alerts and special reports. The news and stories that matter, delivered weekday mornings. In the 2020 election, you might not be able to believe your eyes or your ears due to advances in artificial intelligence that researchers warn could…









Stay connected