1. EXECUTIVE SUMMARY
- CVSS v3 5.9
- ATTENTION: Exploitable remotely
- Vendor: Hitachi Energy
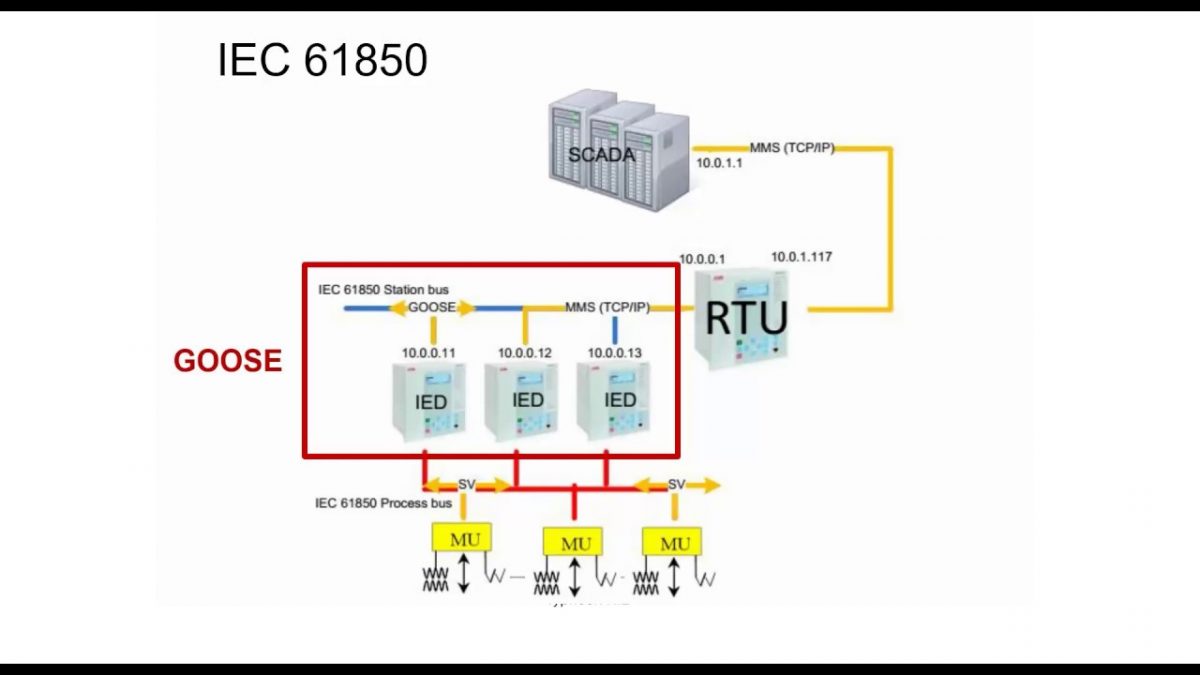
- Equipment: IEC 61850 MMS-Server
- Vulnerability: Improper Resource Shutdown or Release
2. RISK EVALUATION
Successful exploitation of this vulnerability could cause products using the IEC 61850 MMS-server communication stack to stop accepting new MMS-client connections.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
The following versions Hitachi Energy equipment using the IEC 61850 communication stack are affected:
- TXpert Hub CoreTec 4 version 2.0.x
- TXpert Hub CoreTec 4 version 2.1.x
- TXpert Hub CoreTec 4 version 2.2.x
- TXpert Hub CoreTec 4 version 2.3.x
- TXpert Hub CoreTec 4 version 2.4.x
- TXpert Hub CoreTec 4 version 3.0.x
- TXpert Hub CoreTec 5 version 3.0.x
- Tego1_r15b08 (FOX615 System Release R15B)
- Tego1_r2a16_03 (FOX615 System Release R14A)
- Tego1_r2a16
- Tego1_r1e01
- Tego1_r1d02
- Tego1_r1c07
- Tego1_r1b02
- GMS600 version 1.3
- Relion 670 1.2 (Limited)
- Relion 670 2.0 (Limited)
- Relion 650 version 1.1 (Limited)
- Relion 650 version 1.3 (Limited)
- Relion 650 version 2.1 (Classic)
- Relion 670 version 2.1 (Classic)
- Relion SAM600-IO 2.2.1
- Relion SAM600-IO 2.2.5
- Relion 670/650 version 2.2.0
- Relion 670/650 version 2.2.1
- Relion 670/650 version 2.2.2
- Relion 670/650 version 2.2.3
- Relion 670/650 version 2.2.4
- Relion 670/650 version 2.2.5
- ITT600 SA Explorer version 1.1.0
- ITT600 SA Explorer version 1.1.1
- ITT600 SA Explorer version 1.1.2
- ITT600 SA Explorer version 1.5.0
- ITT600 SA Explorer version 1.5.1
- ITT600 SA Explorer version 1.6.0
- ITT600 SA Explorer version 1.6.0.1
- ITT600 SA Explorer version 1.7.0
- ITT600 SA Explorer version 1.7.2
- ITT600 SA Explorer version 1.8.0
- ITT600 SA Explorer version 2.0.1
- ITT600 SA Explorer version 2.0.2
- ITT600 SA Explorer version 2.0.3
- ITT600 SA Explorer version 2.0.4.1
- ITT600 SA Explorer version 2.0.5.0
- ITT600 SA Explorer version 2.0.5.4
- ITT600 SA Explorer version 2.1.0.4
- ITT600 SA Explorer version 2.1.0.5
- MSM version 2.2.3 and prior
- PWC600 version 1.0
- PWC600 version 1.1
- PWC600 version 1.2
- REB500 all V8.x versions
- REB500 all V7.x versions
- RTU500 series CMU Firmware version 12.0.1 to 12.0.14
- RTU500 series CMU Firmware version 12.2.1 to 12.2.11
- RTU500 series CMU Firmware version 12.4.1 to 12.4.11
- RTU500 series CMU Firmware version 12.6.1 to 12.6.8
- RTU500 series CMU Firmware version 12.7.1 to 12.7.4
- RTU500 series CMU Firmware version 13.2.1 to 13.2.5
- RTU500 series CMU Firmware version 13.3.1 to 13.3.3
- RTU500 series CMU Firmware version 13.4.1
- SYS600 version 10.1 to 10.3.1
3.2 VULNERABILITY OVERVIEW
3.2.1 IMPROPER RESOURCE SHUTDOWN OR RELEASE CWE-404
An attacker could exploit the IEC 61850 MMS-Server communication stack by forcing the communication stack to stop accepting new MMS-client connections.
CVE-2022-3353 has been assigned to this vulnerability. A CVSS v3.1 base score of 5.9 has been calculated; the CVSS vector string is (AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Energy
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Switzerland
3.4 RESEARCHER
Hitachi Energy reported this vulnerability to CISA.
4. MITIGATIONS
Hitachi Energy provided updates for the following products. Contact Hitachi Energy for update information.
- MSM Server update to version 2.2.5
- tego1_r15b08 (FOX615 System Release R15B) update to tego1_r16a11 (FOX615 System Release R16A)
- REB500 all V8.x versions update to REB500 firmware to version 8.3.3.0 when released.
- RTU500 series CMU Firmware version 12.0.1 to 12.0.14 Update to CMU Firmware version 12.0.15
- RTU500 series CMU Firmware version 12.2.1 to 12.2.11 Update to CMU Firmware version 12.2.12
- RTU500 series CMU Firmware version 12.4.1 to 12.4.11 Update to CMU Firmware version 12.4.12
- RTU500 series CMU Firmware version 12.6.1 to 12.6.8 Update to CMU Firmware version 12.6.9
- RTU500 series CMU Firmware version 12.7.1 to 12.7.4 Update to CMU Firmware version 12.7.5
- RTU500 series CMU Firmware version 13.2.1 to 13.2.5 Update to CMU Firmware version 13.2.6
- RTU500 series CMU Firmware version 13.3.1 to 13.3.3 Update to CMU Firmware version 13.3.4
- RTU500 series CMU Firmware version 13.4.1 Update to CMU Firmware version 13.4.2
- SYS600 version 10.1 to 10.3.1 update to SYS600 version 10.4.1
For all versions, Hitachi Energy recommends that users apply these general mitigation factors:
- Upgrade the system once a remediated version is available.
- Apply Hitachi Energy recommended security practices and firewall configurations to help protect a process control network from attacks that originate from outside the network. Such practices include:
- Physically protecting process control systems from direct access by unauthorized personnel.
- Not allowing direct connections to the internet.
- Process control systems should not be used for internet surfing, instant messaging, or receiving emails.
- Use a firewall system that has a minimal number of exposed ports to separate the process control network from other networks.
- Connection to other networks must be evaluated as necessary.
- Scan portable computers and removable storage media carefully for viruses before connection to a control system.
- MSM is not designed nor intended to be connected to the internet. Disconnect the device from any internet facing network.
- Adopt user access management and updated antivirus protection engines equipped with the latest signature rules for computers that have installed and are operating the MMS Client application.
- Use the default operating system (OS) user access management function to limit unauthorized access and/or rogue commands via the MMS Client application.
For more information, see the Hitachi Energy advisories for the corresponding affected products:
- 8DBD000124 TXpert Hub CoreTec 4 and 5 Products
- 8DBD000132 RTU500 series
- 8DBD000127 Relion 670, 650 series, and SAM600-IO
- 8DBD000131 REB500 series
- 8DBD000130 PWC600
- 8DBD000129 MSM
- 8DBD000133 MicroSCADA X SYS600
- 8DBD000128 ITT600 SA Explorer
- 8DBD000126 GMS600
- 8DBD000125 FOX61x TEGO1
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage at cisa.gov/ics. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
Source:
https://www.cisa.gov/news-events/ics-advisories/icsa-23-089-01

Stay connected