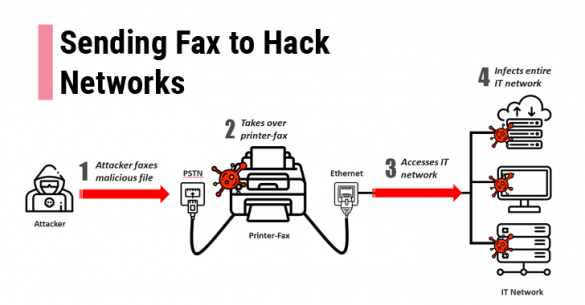
Hackers can compromise your network just by sending a Fax
What maximum a remote attacker can do just by having your Fax machine number? Believe it or not, but your fax number is literally enough for a hacker to gain complete control over the printer and possibly infiltrate the rest of the network connected to…
Oracle warns of CVE-2018-3110 Critical Vulnerability in Oracle Database product, patch it now!
Last week Oracle disclosed a critical vulnerability in its Oracle Database product, the issue tracked as CVE-2018-3110 has received a CVSS score of 9.9, On Friday, Oracle released security patches to address a critical vulnerability affecting its Database product, the company is urging install them as soon…
Hackers Exploiting DLink Routers to Redirect Users to Fake Brazilian Banks
Attackers are targeting DLink DSL modem routers in Brazil and exploiting them to change the DNS settings to a DNS server under the attacker’s control. This then allows them to redirect users attempting to connect to their online banks to fake banking websites that steal the…
Flaw exposed Comcast Xfinity customers’ partial home addresses and SSNs
Poor security measures have reportedly put the personal details of Comcast Xfinity customers at risk, a researcher has revealed. According to a BuzzFeed News report, security researcher Ryan Stevenson found a vulnerability in the high-speed ISP’s online customer portal that could allow unauthorised parties to determine the…
Linux vulnerability could lead to DDoS attacks
A Linux kernel vulnerability affecting version 4.9 and up could allow an attacker to carry out denial-of-service attacks on a system with an available open port, according to an Aug 6 security advisory from the CERT Coordination Center at Carnegie Mellon University’s Software Engineering Institute. “Linux kernel…
DeepLocker: How AI Can Power a Stealthy New Breed of Malware
Cybersecurity is an arms race, where attackers and defenders play a constantly evolving cat-and-mouse game. Every new era of computing has served attackers with new capabilities and vulnerabilities to execute their nefarious actions. In the PC era, we witnessed malware threats emerging from viruses and…
Ramnit is back and contributes in creating a massive proxy botnet, tracked as ‘Black’ botnet
Security researchers at Checkpoint security have spotted a massive proxy botnet, tracked as ‘Black’ botnet, created by Ramnit operators. Security researchers at Checkpoint security have spotted a massive proxy botnet, tracked as ‘Black’ botnet, that could be the sign of a wider ongoing operation involving…
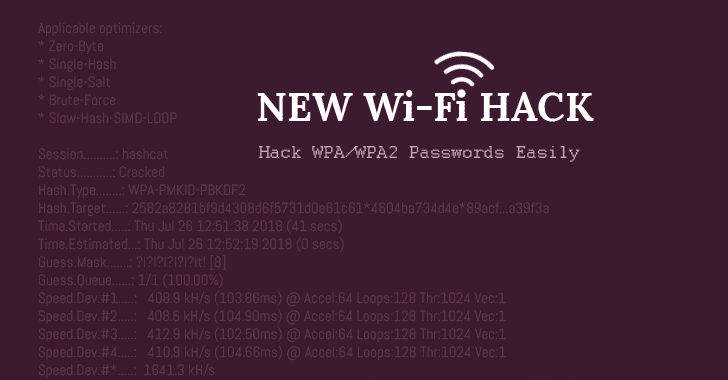
How to Hack WiFi Password Easily Using New Attack On WPA
Looking for how to hack WiFi password OR WiFi hacking software? Well, a security researcher has revealed a new WiFi hacking technique that makes it easier for hackers to crack WiFi passwords of most modern routers. Discovered by the lead developer of the popular password-cracking tool…
Microsoft Edge Flaw Lets Hackers Steal Local Files
Microsoft has fixed a vulnerability in the Edge browser that could be abused against older versions to steal local files from a user’s computer. The good news is that social engineering is involved in exploiting the flaw, meaning the attack cannot be automated at scale,…
DEF CON plans to show US election hacking is so easy kids can do it
Exploit contest opened for tykes – meanwhile, Republicans kill new funding for election security DEF CON Last year, the hackers at DEF CON showed how shockingly easy it was to crack into voting machine software and hardware. Next week, the 2018 conference’s Vote Hacking Village will let kids…








Stay connected