LiteSpeed Cache Plugin Vulnerability Poses Significant Risk to WordPress Websites
A high-severity security flaw has been disclosed in the LiteSpeed Cache plugin for WordPress that could allow an unauthenticated threat actor to elevate their privileges and perform malicious actions. The vulnerability, tracked as CVE-2024-50550 (CVSS score: 8.1), has been addressed in version 6.5.2 of the…
DragonForce Ransomware Expands RaaS, Targets Firms Worldwide
DragonForce ransomware is expanding its RaaS operation and becoming a global cybersecurity threat against businesses. Companies must implement strong cybersecurity strategies to defend against this growing ransomware attack and avoid becoming victims. Ransomware attacks are growing, leaving organizations vulnerable to new and more sophisticated threats. According…
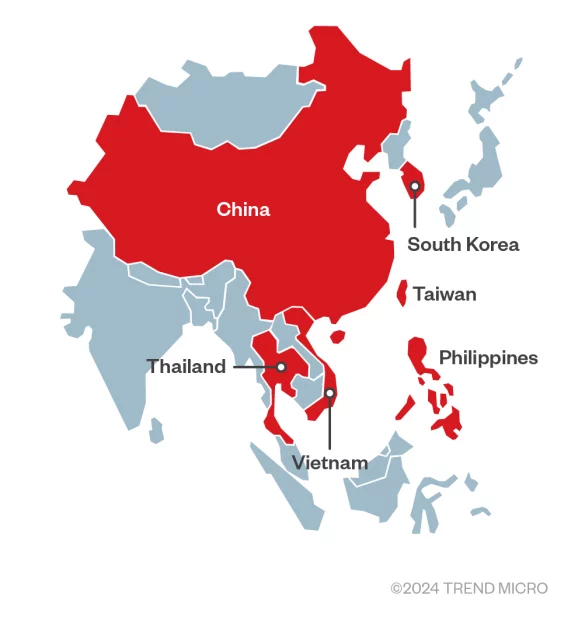
Chinese APT Earth Baxia target APAC by exploiting GeoServer flaw
Suspected China-linked APT Earth Baxia targeted a government organization in Taiwan by exploiting a recently patched OSGeo GeoServer GeoTools flaw. Trend Micro researchers reported that China-linked APT group Earth Baxia has targeted a government organization in Taiwan and potentially other countries in the Asia-Pacific (APAC)…
Hackers claim to have breached Israeli nuclear facility’s computer network
An Iran-linked hacking group claims to have breached the computer network of a sensitive Israeli nuclear installation in an incident declared by the ‘Anonymous’ hackers as a protest against the war in Gaza. The hackers claim to have stolen and published thousands of documents —…
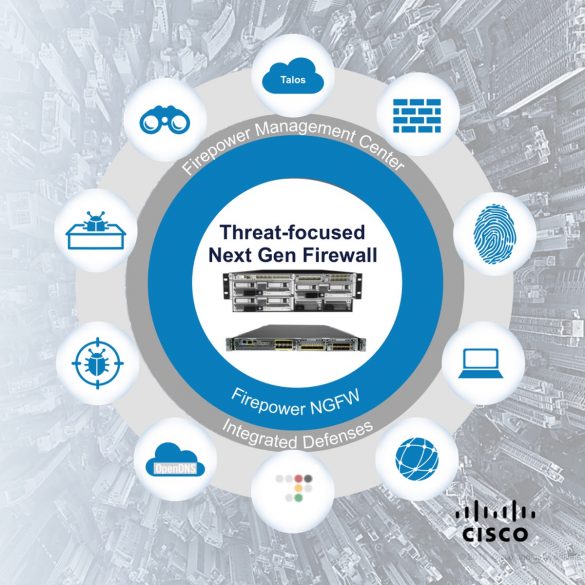
Cisco Firepower Threat Defense Software for Cisco Firepower 2100 Series Firewalls Inspection Rules Denial of Service Vulnerability
Summary Affected Products Indicators of Compromise Workarounds Fixed Software Source:
48 Malicious npm Packages Found Deploying Reverse Shells on Developer Systems
A new set of 48 malicious npm packages have been discovered in the npm repository with capabilities to deploy a reverse shell on compromised systems. “These packages, deceptively named to appear legitimate, contained obfuscated JavaScript designed to initiate a reverse shell on package install,” software…
Apple iOS, iPadOS, and watchOS Wallet Code Execution CVE-2023-41061
Description A validation issue was addressed with improved logic. This issue is fixed in watchOS 9.6.2, iOS 16.6.1 and iPadOS 16.6.1. A maliciously crafted attachment may result in arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited….
Mitsubishi Electric MELSEC Series CPU module
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to cause a denial-of-service condition or execute malicious code on a target product by sending specially crafted packets. The attacker needs to understand the internal structure of products to…
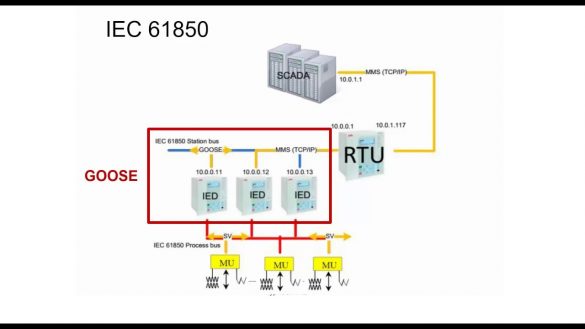
Hitachi Energy IEC 61850 MMS-Server
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could cause products using the IEC 61850 MMS-server communication stack to stop accepting new MMS-client connections. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions Hitachi Energy equipment using the IEC 61850 communication stack…
CISA Releases Phishing Infographic
CISA published a Phishing Infographic to help protect both organizations and individuals from successful phishing operations. This infographic provides a visual summary of how threat actors execute successful phishing operations. Details include metrics that compare the likelihood of certain types of “bait” and how commonly…







Stay connected