Mitsubishi Electric GOT and Tension Controller (Update A)
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Mitsubishi Electric Equipment: GOT and Tension Controller Vulnerabilities: Improper Handling of Exceptional Conditions, Improper Input Validation ——— Begin Update A Part 1 of 2 ——— Mitsubishi Electric PSIRT has informed CISA that further research has shown the…
Delta Electronics DOPSoft
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Delta Electronics Equipment: DOPSoft Vulnerabilities: Out-of-bounds Write, Untrusted Pointer Dereference 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow arbitrary code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of DOPSoft, a software…
Phoenix Contact Automation Worx Software Suite
1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: Phoenix Contact Equipment: Automation Worx Software Suite Vulnerabilities: Stack-based Buffer Overflow, Out-of-Bounds Read 2. RISK EVALUATION Successful exploitation could allow an attacker to execute arbitrary code under the privileges of the application. 3. TECHNICAL DETAILS 3.1…
Website of gunmaker Smith & Wesson hit by a Magecart attack
The US gunmaker Smith & Wesson was hacked late last month in a Magecart attack, attackers injected a malicious software skimmer. A new Magecart attack made the headlines, the victim is the American gunmaker Smith & Wesson. The hack took place last month, the attackers planted a malicious software skimmer on…
Chinese Hackers Use New Malware to Backdoor Microsoft SQL Servers
New malware created by Chinese-backed Winnti Group has been discovered by researchers at ESET while being used to gain persistence on Microsoft SQL Server (MSSQL) systems. The new malicious tool dubbed skip-2.0 can be used by the attackers to backdoor MSSQL Server 11 and 12 servers, enabling them to connect to any…
At least 1,300 Harbor cloud registry installs open to attack
A critical security flaw in Harbor cloud native registry for container images could be exploited to obtain admin privileges on a vulnerable hosting system. Palo Alto Networks’ Unit 42 researcher Aviv Sasson discovered a critical vulnerability in Harbor cloud native registry for container images. The flaw, tracked as CVE-2019-16097,…
3S-Smart Software Solutions GmbH CODESYS V3 Web Server
1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: 3S-Smart Software Solutions GmbH Equipment: CODESYS V3 web server Vulnerabilities: Path Traversal, Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities may allow an attacker to create a denial-of-service condition, to perform remote…
Hackers are exploiting a platform-agnostic flaw to track mobile phone locations
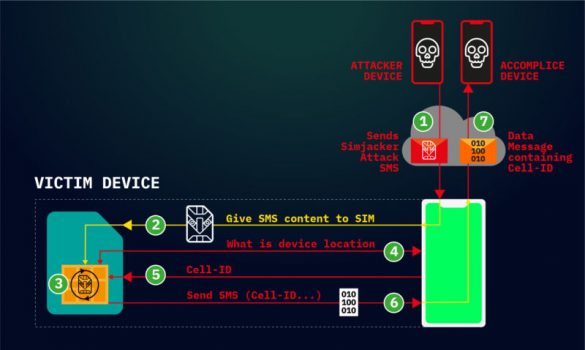
Attacks work by sending commands directly to applications stored on SIM cards. Hackers are actively exploiting a critical weakness found in most mobile phones to surreptitiously track the location of users and possibly carry out other nefarious actions, researchers warned on Thursday. The so-called Simjacker…
Hacking IoT hackers: How to crash Mirai IoT command and control servers
Introduction Just like every piece of software code, malware are not immune to vulnerabilities. In fact, most malware do not go through the process of Quality Control, and have more probability to have a bug. Sometimes these bugs can be (mis)used for various motives. In…
New DNS Hijacking Attacks
DNS hijacking isn’t new, but this seems to be an attack of uprecidented scale: Researchers at Cisco’s Talos security division on Wednesday revealed that a hacker group it’s calling Sea Turtle carried out a broad campaign of espionage via DNS hijacking, hitting 40 different organizations. In the…








Stay connected