Hitachi Energy’s AFS65x, AFS67x, AFR67x and AFF66x Products
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to disclose sensitive information or lead to a Denial-of-Service (DoS). 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Hitachi Energy’s AFS65x, AFS67x, AFR67x and AFF66x series products, are…
Mitsubishi Electric MELSEC Series CPU module
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow a remote attacker to cause a denial-of-service condition or execute malicious code on a target product by sending specially crafted packets. The attacker needs to understand the internal structure of products to…
Siemens SIMATIC Cloud Connect 7
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to execute arbitrary code. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products from Siemens are affected: 3.2 VULNERABILITY OVERVIEW 3.2.1 IMPROPER NEUTRALIZATION OF SPECIAL ELEMENTS USED IN A COMMAND (‘COMMAND…
Siemens SCALANCE W1750D
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to disclose sensitive information or steal the unsuspecting user’s session. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products from Siemens are affected: 3.2 VULNERABILITY OVERVIEW 3.2.1 IMPROPER INPUT VALIDATION CWE-20…
Industrial Control Links ScadaFlex II SCADA Controllers
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an authenticated attacker to overwrite, delete, or create files. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Industrial Control Links ScadaFlex II SCADA Controllers are affected: 3.2 VULNERABILITY OVERVIEW 3.2.1 EXTERNAL…
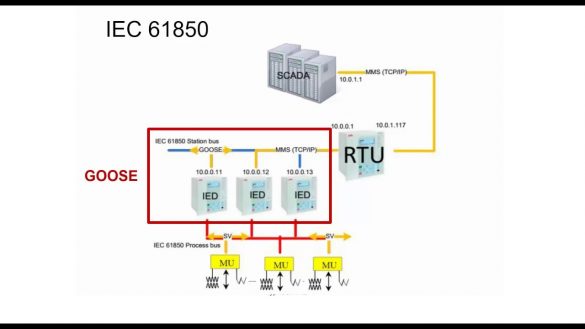
Hitachi Energy IEC 61850 MMS-Server
1. EXECUTIVE SUMMARY 2. RISK EVALUATION Successful exploitation of this vulnerability could cause products using the IEC 61850 MMS-server communication stack to stop accepting new MMS-client connections. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions Hitachi Energy equipment using the IEC 61850 communication stack…
Siemens RADIUS Client of SIPROTEC 5 Devices
1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens ProductCERT Equipment: RADIUS client of SIPROTEC 5 devices Vulnerability: Loop with Unreachable Exit Condition (‘Infinite Loop’) 2. RISK EVALUATION The RADIUS client implementation of the VxWorks platform in SIPROTEC 5 devices contains a denial-of-service vulnerability that…
Cisco Releases Security Advisory for IOS XR Software
Cisco has released a security advisory for a vulnerability affecting IOS XR Software for ASR 9000 Series Routers. A remote attacker could exploit this vulnerability to cause a denial-of-service condition. For updates addressing lower severity vulnerabilities, see the Cisco Security Advisories page. CISA encourages users and administrators to…
AVEVA Plant SCADA and AVEVA Telemetry Server
1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: AVEVA Equipment: AVEVA Plant SCADA and AVEVA Telemetry Server Vulnerability: Improper Authorization 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an unauthenticated user to read data, cause a denial of service, and tamper with…
Siemens SIMATIC Industrial Products
1. EXECUTIVE SUMMARY CVSS v3 7.9 ATTENTION: Low attack complexity Vendor: Siemens Equipment: SIMATIC industrial products Vulnerability: Time-of-check Time-of-use (TOCTOU) Race Condition 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a privileged user to potentially enable escalation of privilege via local access. 3. TECHNICAL DETAILS 3.1 AFFECTED…









Stay connected