mangOH Open Source platform launched by Sierra Wireless to accelerate industrial IoT, expands mangOH ecosystem
Sierra Wireless, a provider of integrated device-to-cloud solutions for the Internet of Things (IoT), has released alpha samples of its next-generation mangOH® open source hardware platform. The company is also inviting the IoT developer community to influence the final product. mangOH Yellow, a “super sensor” for connected IoT, allows developers to…
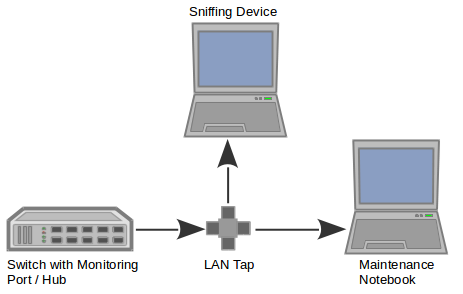
Performing Passive Analysis of Process Control Networks (PCNs)
In recent years there has been an increased push to secure critical ICS infrastructures by introducing information security management systems. One of the first steps in the ISMS lifecycle is to identify which assets are present in the infrastructure and to determine which ones are…
You’re probably doing your IIoT implementation wrong
The Industrial Internet of Things promises a quantum leap forward in automation, centralized management and a wealth of new data and insight that is often too tempting to pass up. But automating a factory floor or a fleet of vehicles is far from simple, and…
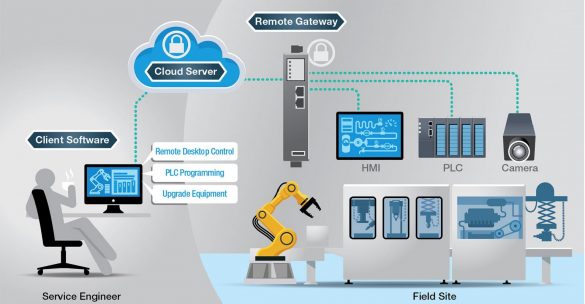
Five Issues Facing Secure Remote Access to IIoT Machines
The Industrial Internet of Things (IIoT) is changing the way business owners view their factories by giving them real-time data from machines and devices in the field that let them monitor and control production. Overall equipment effectiveness (OEE) and zero equipment downtime are no longer…
Progress Launches AWS-Backed IIoT Anomaly Detection Service
Progress announced on Thursday the launch of a new self-service anomaly detection and prediction option for the IIoT market that leverages AWS. Application development and deployment company Progress announced on Thursday the launch of a new self-service anomaly detection and prediction option for the Industrial…
Particle Mesh – A Mesh-Enabled IoT Development Kits.
Particle, which has been known for its collection of IoT focused development boards, and its Internet of Things (IoT) platform (Particle Cloud) has launched a new set of mesh network-enabled IoT development kits called Particle Mesh. Particle Mesh is expected to provide developers more insight…
Intelligent IoT Vulnerability Scanner for communication service providers launched to assess and predict cybersecurity risks
Dojo by BullGuard, a provider of IoT security platform for Communication Service Providers (CSPs), has launched the Dojo Intelligent IoT Vulnerability Scanner for CSPs. Designed as an easy-to-use, free app for customers, the Dojo Intelligent Scanner is powered by the Dojo IoT Security Intelligent Platform (DIP), a…
How Mirai spawned the current IoT malware landscape
When, in late 2016, US-based DNS provider Dyn suffered a massive DDoS attack that it resulted in the temporary unavailability of many popular online services, the name of the Mirai malware became instantly known outside the cybersecurity industry. Since then, we’ve come to know the…
Operation Prowli Profits On Weak IoT Devices, Servers
A malicious campaign has compromised more than 40,000 machines globally, carrying out traffic-hijacking and cryptomining. Researchers at Guardicore Labs, who called the campaign Operation Prowli, said it targets a variety of platforms – including Drupal CMS websites, WordPress sites, backup servers running HP Data Protector,…
Russia asks Apple to remove Telegram Messenger from the App Store
Russia’s communications regulator Roskomnadzor has threatened Apple to face the consequences if the company does not remove secure messaging app Telegram from its App Store. Back in April, the Russian government banned Telegram in the country for the company’s refusal to hand over private encryption…









Stay connected